D CEO Healthcare
The Business of Healthcare in North Texas

Healthcare
Convicted Dallas Anesthesiologist Could Face 190 Years for ‘Toxic Cocktails’ in IV Bags
Dr. Raynaldo Ortiz worked at the Baylor Scott & White Health facility after spending time in jail for shooting a dog and previous Texas Medical Board discipline.
By Will Maddox
Advertisement
Trending
Advertisement
Latest

Healthcare
North Texas Healthcare Compensation: Who’s On Top?
Executives at Tenet Healthcare, McKesson Corp., and CHRISTUS Health lead the way.
By Will Maddox

News
Medical City Dallas’ New CEO and Hospitals Recognized for Price Transparency
Plus Texas Urology Specialists expands in North Texas and Business Group on Health honors Texas Health.
By Bridget Reis

Healthcare
Convicted Dallas Anesthesiologist Could Face 190 Years for ‘Toxic Cocktails’ in IV Bags
Dr. Raynaldo Ortiz worked at the Baylor Scott & White Health facility after spending time in jail for shooting a dog and previous Texas Medical Board discipline.
By Will Maddox

Policy
As Mississippi Nears Medicaid Expansion, Could Texas Be Next?
An Episcopal Health Foundation study found that Texas loses $7 billion in healthcare and lost productivity costs each year due to health disparities.
By Will Maddox

News
DFWHC’s Steve Love Named Chair-Elect of Irving Chamber and Medical City Again Wins ‘Best Place to Have a Baby’
Plus Red River Hospital's New CEO and Texas Recognized by Fortune as Best Place to Work.
By Bridget Reis
Advertisement
Latest
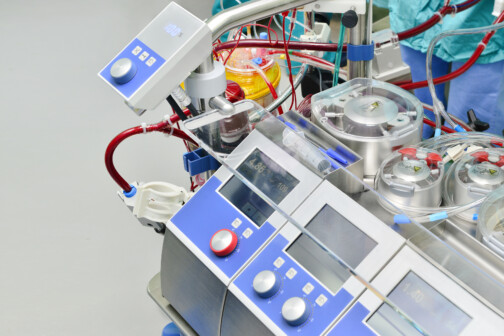
Healthcare
The Local Hospital Using Heat to Treat Cancer
First Baptist Medical Center is one of the only places in the country offering the innovative treatment.
By Will Maddox

Healthcare
How Lantern Pharma’s AI Is Changing the Game
The precision oncology medicine company guided three drugs in the trial pipeline with uncommon efficiency.
By Will Maddox

Crime
Irving Man Sentenced for $7 Million COVID Testing Fraud
After being charged in 2022 and pleading guilty last fall, Terrance Barnard was sentenced to seven years for defrauding private insurers with stolen patient data.
By Will Maddox

Dallas 500
Meet the Dallas 500: Robert Walker, Scottish Rite for Children
The hospital president and CEO shares how he developed his work ethic, how he spends his free time, and what he sees in store for the health system.
By Will Maddox

News
Dr. Raynaldo Ortiz’s IV Tampering Trial Begins and Tenet Sells Six More Hospitals
Plus Steward's Sells Physician Group, Southern Dallas hospital housing question, and more.
By Bridget Reis

